Protect Yourself from Government Surveillance with these online privacy tips

I like Wired magazine; it’s the only magazine I subscribe to these days (although I mainly read it online). I have been disappointed by their editorial choices lately, however. In particular, a recent story of useful online privacy tips disappointed by using fear mongering about Trump’s re-election in an attempt to boost organic web traffic.
The gist of the story is that, based upon some of the more incendiary and irresponsible things Trump has said about his critics and political foes, there are those who fear a Trump presidency will lead to an increase in domestic government surveillance, targeted both at foreign nationals and the President’s enemies, many of whom are U.S. citizens.
While the President does have a significant amount of authority over the American spy apparatus (namely, the National Security Agency or NSA, which is within the Executive Branch and whose director reports directly to the President), there is no evidence surveillance increased during Trump’s first term, let alone that he plans to do so in his upcoming term. Wired should leave stories like this one where they belong, on Twitter or Reddit. It’s a slippery slope to write news about rumors.
It’s also a self-defeating strategy to publish stories that are so clearly biased. It just makes Trump’s complaints about the media (“fake news!”) appear reasonable. And since when did objective reporting become so out-of-fashion? If I had to guess I’d say around the time the cookie was invented.
Another problem with the Wired story is that the actual meat of it — the useful privacy recommendations — appear to be recycled from an older story, which is fine, that’s a reality of online publishing… but before reporting an old story in a new wrapper, make sure the information is still relevant and accurate. Technology changes rapidly, after all.
Wired didn’t do that, or didn’t do it well. In particular, they forgot about Apple’s update to iCloud that brings end-to-end encryption to the service. There are a few other oversights and omissions as well. They have been corrected in my summary below, which should serve as a more useful and practical guide for anyone concerned about government surveillance.
Online Privacy Tips:
1. use Messaging Apps with end-to-end encryption.
Be careful when you just see the word encryption describing a messaging app. If it doesn’t include the qualifier end-to-end, then it’s not as secure as you think. The word encryption in the context of a messaging app usually refers to encryption of the message during transit, but not on the servers of its parent company. In order for communications to truly be private and secure, a messaging app must utilize end-to-end encryption. That means nobody at the app’s parent company can decrypt and read these messages, which means they can’t respond to a government subpoena for it.
Only a few messaging apps offer end-to-end encryption: Signal (favored by Edward Snowden), WhatsApp, and Apple’s iMessage/FaceTime. Of these, Signal comes most highly recommended because its parent company doesn’t even store metadata about messages sent on the platform (a lot of inferences can be made based on metadata). Signal may not have all the bells and whistles of an app like Telegram, but nobody trusts Telegram these days.

2. Encrypt all of your devices.
Make sure you turn on FileVault on your Mac computer or BitLocker on your Windows computer to encrypt your computer hard drives (these are turned off by default). Also, make sure you use a phone that is encrypted. All iPhones became full-disk encrypted starting with iOS 8, which was released in 2014. Android phones are also encrypted. For additional security, Wired recommends you change your 6-digit numeric password to a longer alphanumeric one. And be aware that encryption is harder to crack when a device is turned off, so turn off your devices whenever possible, especially before that political rally or border crossing.

3. Avoid Most cloud services.
Cloud services are oh-so-convenient, but they are also inherently insecure, and it’s not just radicals and revolutionaries that need to be concerned. That’s because the biggest threat to data in the cloud comes from hackers. A data breach could result in your personal photos, emails, and financial documents ending up on the dark web, and breaches are becoming more common, especially in the U.S.
For those who simply must use a cloud service, Wired recommends encrypting files prior to uploading them to the cloud, and recommends the open-source tool Veracrypt for that purpose. I would also recommend MacPaw’s Encrypto as a more user-friendly alternative. Pre-encrypting one’s cloud data may be overkill, however, for users of Apple’s iCloud, due to an important security update Wired neglected to mention.
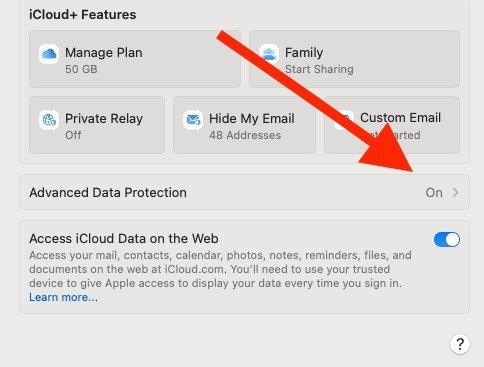
For a couple of years now, Apple has offered end-to-end encryption (there’s that word again) in iCloud via a feature Apple calls Advanced Data Protection. It is turned off by default, so you’ll have to be proactive in setting it up. It can be found in System Settings on your Mac computer, and in iCloud settings on your iPhone or iPad. Once this feature is turned on, however, users need to be very careful with their password or decryption key. If a user ever gets locked out of iCloud, Apple won’t be able to help them get back in. Which is why, of course, this feature is turned off by default.
4. Browse the Web using Tor or a VPN.
Wired recommends readers browse the web with the Tor browser, because it doesn’t track web activity. If this is too big of an ask — and for many people it is — then the article recommends using a trusted VPN alongside one’s browser of choice. Wired declined to recommend a VPN or a browser alternative, but I have no such qualms.
As far as mainstream browsers go, Firefox is the most committed to privacy (it eliminated third party cookies years ago, for instance), but using it will not hide one’s tracks on the web. That’s where NordVPN comes in, which I recommend with one caveat: turn off the IPv6 protocol on your computer first. Nord only obfuscates web traffic sent over the IPv4 protocol, but this essential piece of limitation is buried in its documentation. If IPv6 is turned on and your internet provider is Comcast or one of a few select others, NordVPN will appear to be operating correctly but your web activity will be exposed.
To test whether your VPN is actually working and that your web tracks are hidden online, test it with a tool like IPLeak.
5. Beware of Location data.
And finally, Wired recommends turning off location data on your phone for as many services as possible. Of course, that will render many apps useless, so the task will surely turn out to be easier said than done. However, location data is everything. It’s how the January 6 protesters were caught, after all. If you really want to keep your movements private, switch to an old-school non-smart cell phone. At the very least, leave your phone at home when attending that civil rights rally. Who wants to bet the Jan. 6 protesters wish they had done that?





